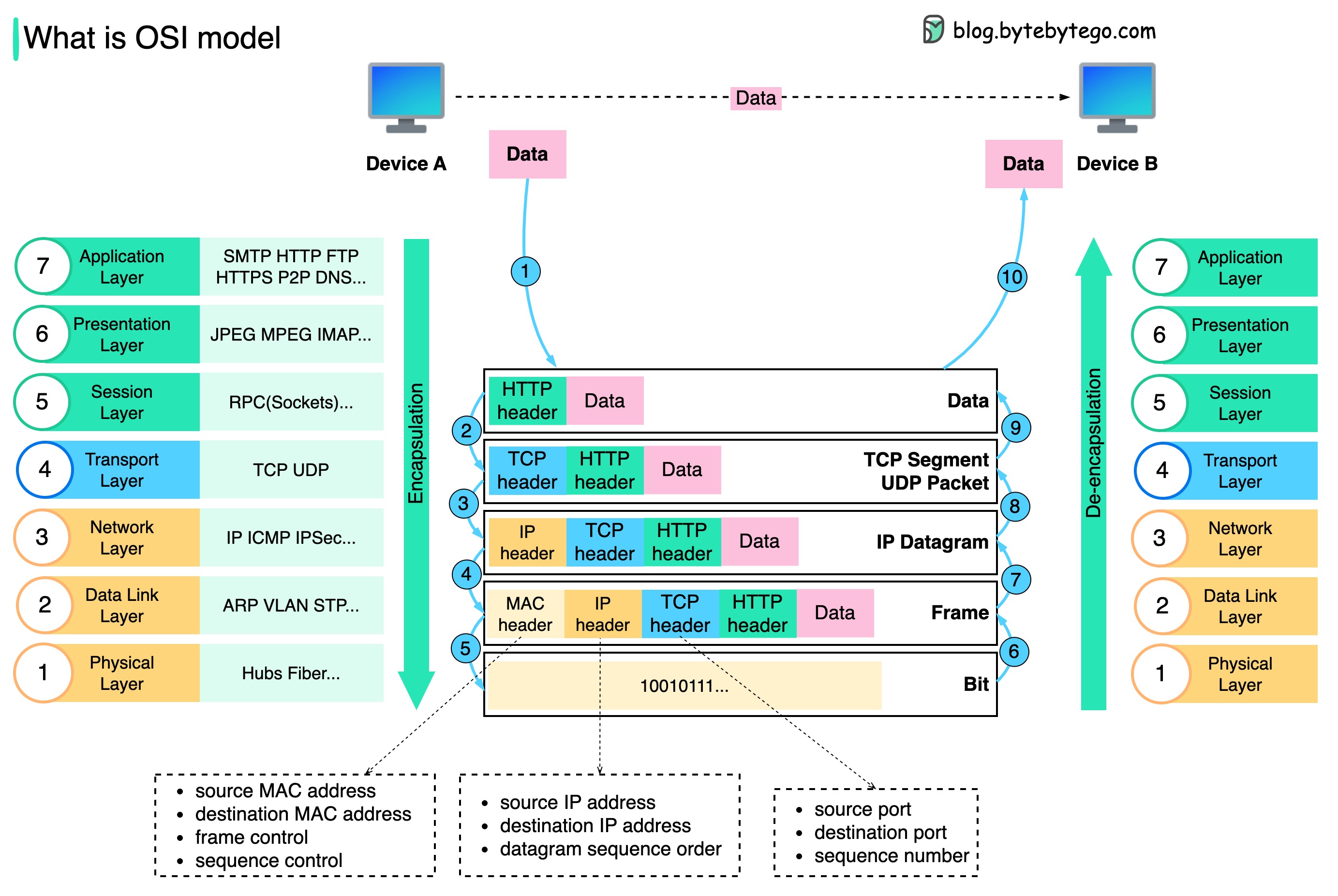
OSI Model
The OSI (Open Systems Interconnection) Model is a conceptual framework that describes how data moves across a network. It breaks communication into seven layers, each with a distinct role—from physical signals up to human-facing applications.
By separating responsibilities, the OSI model makes it easier to design, troubleshoot, and scale networks. Each higher layer builds on the services of the one below, while remaining logically independent.
1. The 7 Layers
| Layer | Example Protocols | Data Unit | What It Adds / Handles | Notes |
|---|---|---|---|---|
| L7 Application | HTTP, DNS, SMTP, FTP | Data | User-facing services | Browser → HTTP, Mail → SMTP. |
| L6 Presentation | TLS/SSL, JPEG, JSON | Record | Data format, encryption, compression | Often merged into L7. |
| L5 Session | NetBIOS, RPC | – | Session setup & teardown | Rarely explicit today. |
| L4 Transport | TCP, UDP | Segment | Reliable (TCP) vs fast (UDP) | TCP = handshake, ports, seq/ack. UDP = stateless. |
| L3 Network | IP, ICMP | Packet | Logical addressing & routing | Routers forward packets. Uses ARP for MAC resolution. |
| L2 Data Link | Ethernet, Wi-Fi, PPP | Frame | Local delivery | Frames = MAC headers + payload + CRC. |
| L1 Physical | Copper, Fiber, Wi-Fi PHY | Bits | Transmission of raw signals | Voltage, RF, or optical light. |
🔁 Encapsulation order:
Application Data → Segment → Packet → Frame → Bits
2. Devices at Each Layer
| Device | Layer | What It Does | Protocols | Authentication |
|---|---|---|---|---|
| Load Balancer | L4–L7 | Distributes traffic | TCP, HTTP/S, gRPC | TLS certs, tokens |
| Firewall | L3–L4 (sometimes L7) | Filters packets/flows | IP, TCP/UDP, HTTP | Rules, TLS interception, VPN |
| Router | L3 | Routes IP packets | IP, ICMP, BGP, OSPF | BGP MD5, IPsec |
| Switch | L2 | Forwards frames by MAC | Ethernet, VLAN, ARP | 802.1X, MAC binding |
| Hub | L1 | Repeats bits blindly | – | None |
3. Layer Interactions
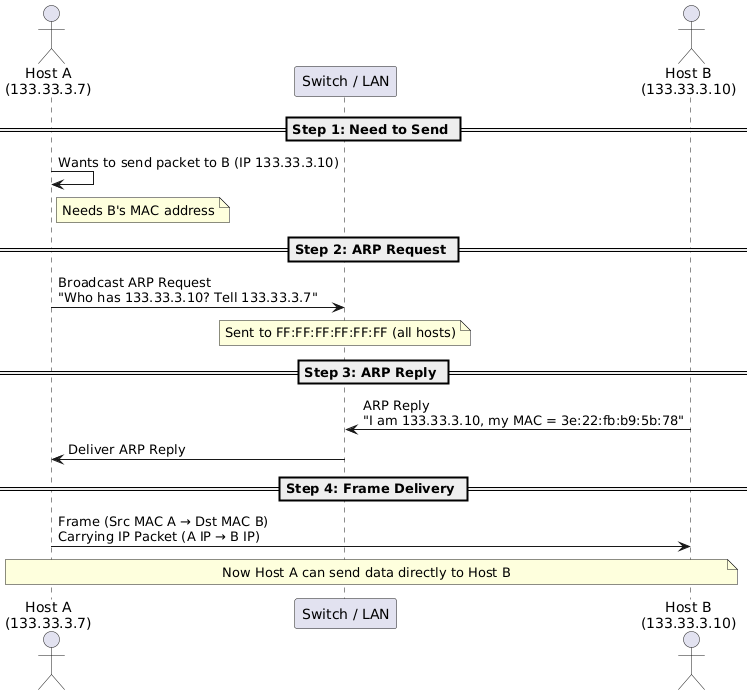
3.1 Layer 2 – ARP
Maps IP → MAC via broadcast request and unicast reply.
3.2 Layer 2 – VLANs & Trunks
VLANs, trunks, and QinQ are needed to segment traffic, reduce broadcast domains, and efficiently carry multiple logical networks over the same physical infrastructure.
- VLAN (802.1Q):
- Adds a VLAN ID tag inside Ethernet frames.
- Splits one physical switch into multiple broadcast domains → improves scalability & security.
- Trunks:
- A single link between switches that carries multiple VLANs using tagging.
- Avoids needing one cable per VLAN.
- QinQ (802.1AD):
- VLAN stacking (two tags: S-Tag + C-Tag).
- Lets ISPs carry customer VLANs over their own backbone.
- Expands VLAN ID space beyond the 4096 limit.
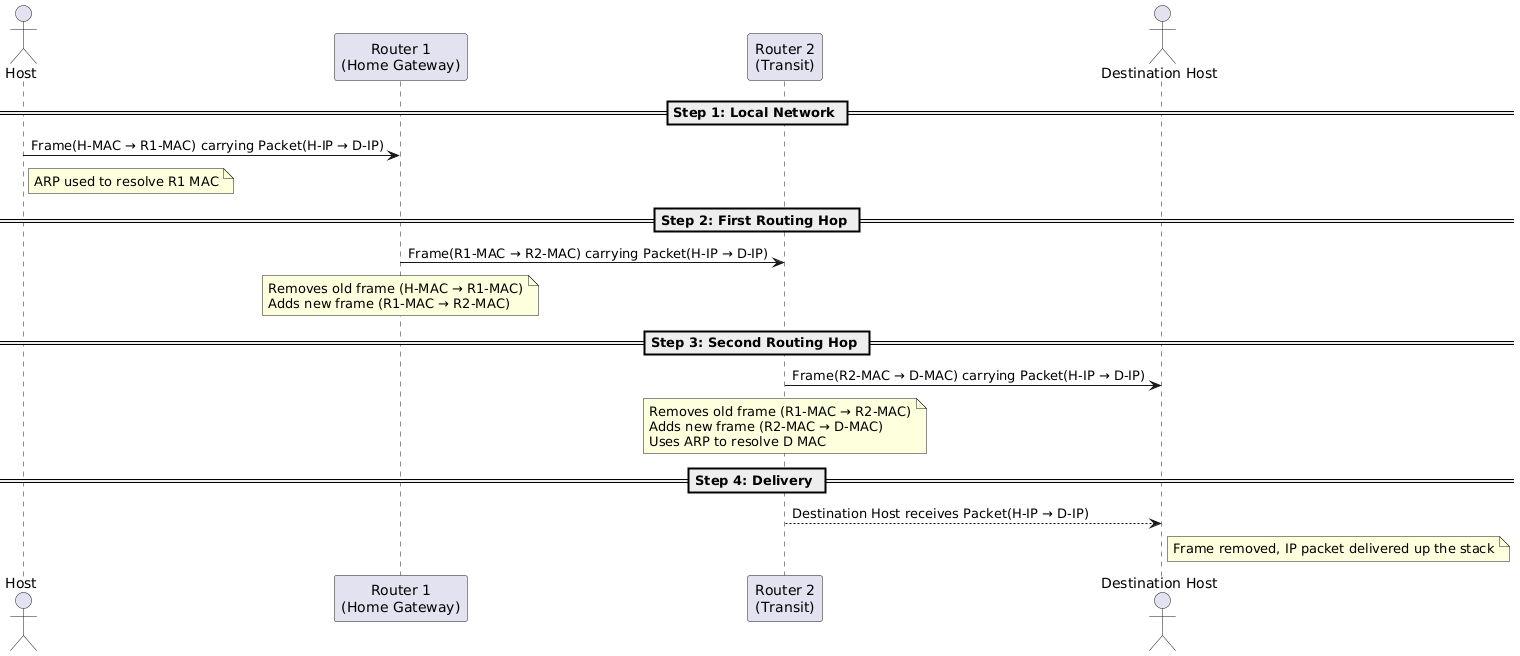
3.3 Layer 3 – Routing
Routers strip old frames, keep IP header, attach new MAC header for next hop.
3.4 Layer 3 & 5–6 - IPsec
IPsec = encrypted network tunnels.
- IKE (control plane) negotiates SAs and keys (Layer 5–6, over UDP/500 or UDP/4500 for NAT-T).
- ESP/AH (data plane) protects IP packets at Layer 3.
- Commonly used for site-to-site and remote-access VPNs.
- Protects all traffic (HTTP, SSH, DNS, ICMP, etc.), independent of app protocol.
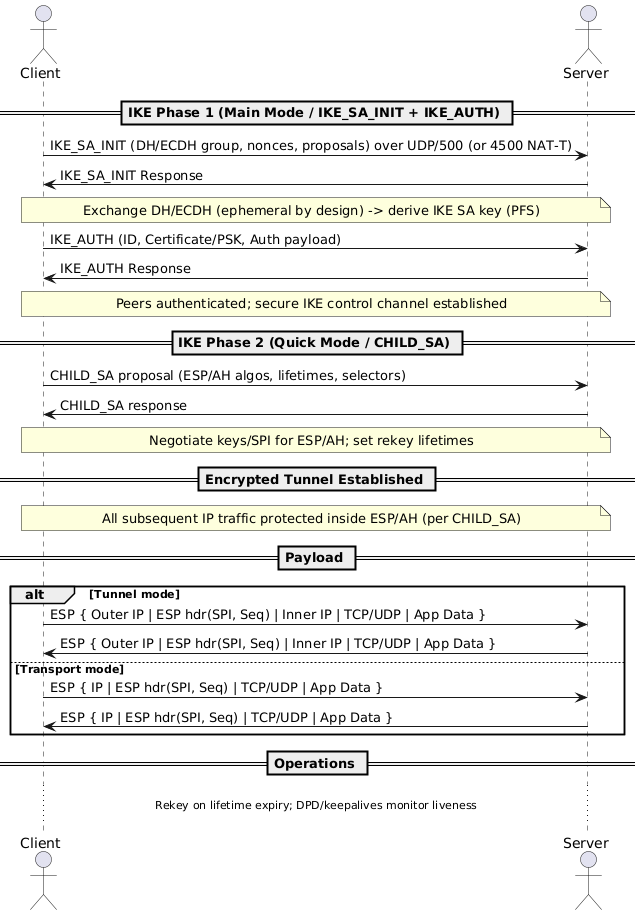
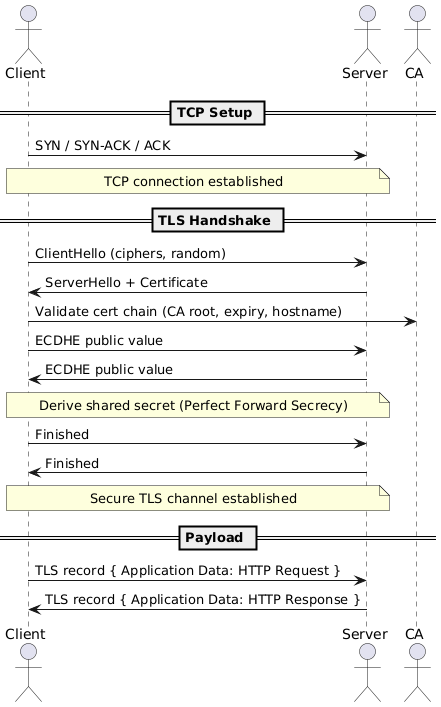
Elliptic Curve Diffie–Hellman Ephemeral provides Perfect Forward Secrecy (PFS) by using a fresh, temporary key pair per session. Even if a server’s long-term private key is later compromised, past sessions remain confidential. Both TLS and IPsec commonly prefer ECDHE for key exchange.
3.5 Layer 5–6 - TLS
TLS = encrypted application sessions.
- Runs above TCP (L4) and below Application (L7).
- Provides confidentiality, integrity, authentication.
- Examples: HTTPS, SMTPS, IMAPS.
- Protects specific app protocols, not all traffic.
3.6 Traffic Addressing Modes (Unicast, Broadcast, Multicast, Anycast, Geocast)
How frames/packets are addressed determines who receives them and how the network treats them.
| Mode | Who Receives | OSI Context | Typical Uses | Key Notes |
|---|---|---|---|---|
| Unicast | Exactly one host | L2 (MAC→MAC), L3 (IP→IP) | Web browsing, API calls, SSH | Most traffic is unicast. Switched at L2, routed at L3. |
| Broadcast | All hosts in the L2 broadcast domain | L2 (FF:FF:FF:FF:FF:FF) | ARP, DHCP DISCOVER | Routers block broadcasts by default. |
| Multicast | Members of a subscribed group | L3 (224.0.0.0/4 IPv4; ff00::/8 IPv6) | IPTV, conferencing, OSPF | Uses IGMP/MLD (hosts), PIM (routers). |
| Anycast | “Nearest” one of many identical endpoints | L3 (same IP announced in multiple sites) | CDNs, DNS resolvers | Routing selects the closest service. |
| Geocast | Hosts in a geographic region | L3 concept | Vehicular alerts, ITS | Conceptual; app-layer in practice. |
4. Commands by OSI Layer
| Layer | Command | Purpose | Example |
|---|---|---|---|
| L2 | arp |
Show ARP cache | arp -a |
| L3 | ping |
Test ICMP reachability | ping 8.8.8.8 |
| L3 | traceroute |
Show hop path | mtr 8.8.8.8 |
| L4 | ss |
List sockets | ss -ant |
| L4 | tcpdump |
Capture packets | tcpdump -i eth0 port 443 |
| L7 | dig |
DNS lookup | dig example.com |
| L7 | curl |
Test HTTP | curl -vk https://site |
| Cross | nmap |
Port scan | nmap -sS 10.1.2.3 |
5. IP Addressing Basics
5.1 IPv4 Classes & Reservations
- Class A: 0.0.0.0 – 127.255.255.255 (10.0.0.0/8 private, 127/8 loopback)
- Class B: 128.0.0.0 – 191.255.255.255 (172.16.0.0/12 private)
- Class C: 192.0.0.0 – 223.255.255.255 (192.168/16 private, TEST-NETs)
- Class D: 224.0.0.0 – 239.255.255.255 (multicast)
- Class E: 240.0.0.0 – 255.255.255.255 (experimental)
5.2 Convert Binary to Decimal
- Take the binary
10000100. -
Multiply each bit by its place value:
- 1×128 + 0×64 + 0×32 + 0×16 + 0×8 + 1×4 + 0×2 + 0×1
- Add them up → 132.
| Position | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | Sum |
|---|---|---|---|---|---|---|---|---|---|
| Decimal | 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 | |
| Bit | 1 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | |
| Value | 128 | 0 | 0 | 0 | 0 | 4 | 0 | 0 | 132 |
👉 So 10000100 in decimal = 132
5.3 Convert Decimal to to Binary
Take the first octet of 132.12.1.23.
- Start from 128 → 132 ≥ 128 → put 1, remainder = 132 − 128 = 4.
- Next (64) → 4 < 64 → 0.
- Next (32) → 4 < 32 → 0.
- Next (16) → 4 < 16 → 0.
- Next (8) → 4 < 8 → 0.
- Next (4) → 4 ≥ 4 → 1, remainder = 0.
- Next (2) → 0 < 2 → 0.
- Next (1) → 0 < 1 → 0.
Result row: 1 0 0 0 0 1 0 0
| Position | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| Decimal | 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
| Representation | 1 | 0 | 0 | 0 | 0 | 1 | 0 | 0 |
👉 So 132 in binary = 10000100
6. Advanced Networking Topics
6.1 NAT (Network Address Translation)
- Allows private IPs (RFC1918) to communicate with public networks.
- Originally designed to conserve IPv4 addresses, also adds a basic security layer by hiding internal hosts.
- Types:
- Static NAT → Fixed 1:1 mapping (one private ↔ one public). Useful for servers that must be reachable externally.
- Dynamic NAT → Private IPs mapped temporarily to an available public IP from a pool. Mapping changes each session.
- PAT (Port Address Translation) → Many private hosts share a single public IP. NAT device rewrites source IP+Port to track flows. Example: home routers, carrier-grade NAT appliances.
6.2 DDoS Attacks (3 categories)
- Volumetric → Flood bandwidth with massive traffic (e.g., UDP floods, DNS/NTP amplification).
- Protocol → Exploit L3/L4 weaknesses, exhausting connection state (e.g., SYN flood, Smurf attack, Ping of Death).
- Application → Target app layer (L7) with valid-looking requests that overwhelm servers (e.g., HTTP floods, Slowloris).
6.3 BGP (Border Gateway Protocol)
The internet is a network of networks (Autonomous Systems, or AS):
- AS (Autonomous System): Collection of IP prefixes under one admin domain.
- ASN (Autonomous System Number): Unique ID (Google = AS15169, Amazon = AS16509).
- BGP Basics: Protocol to exchange routing info between ASes (runs over TCP/179).
- iBGP → Routing inside an AS (e.g., Google’s internal backbone).
- eBGP → Routing between ASes (e.g., ISP ↔ Cloudflare).
- ASPATH: List of AS hops; shortest usually preferred.
- Policies & Tricks:
- ASPATH prepending → make a path look less attractive.
- Route filtering → accept/export only selected prefixes.
- Peering vs Transit → prefer cheap/free peer routes over costly transit.
6.4 Jumbo Frames
- Default MTU = 1500 bytes, Jumbo Frames = ~9000 bytes.
- Benefits: Less overhead, fewer packets, higher throughput for large data transfers.
- Limitations: Must be supported end-to-end; mismatches cause fragmentation or drops.
- Supported in: Local networks, datacenter interconnects, dedicated private backbones, and direct cloud interconnect links.
- Not supported in: General internet, VPN over public internet, cross-region cloud traffic.
6.5 Layer 7 Firewalls
- Extend firewalls beyond L3/L4 (IP, port) to application-aware filtering at L7.
- Parse and inspect protocols (HTTP, DNS, SMTP, gRPC).
- Capabilities:
- Block/allow traffic based on URLs, headers, payloads.
- Detect and stop application-layer DDoS (HTTP floods, bots).
- Enforce auth/security policies (tokens, TLS inspection).
- Examples: Cloudflare WAF, Palo Alto NGFW, F5 ASM, Imperva SecureSphere.
7. Domain Name System (DNS)
7.1 What DNS Does
DNS (Domain Name System) maps human-readable names (e.g., example.com) to IP addresses or other service endpoints. Two roles often get conflated:
- DNS hosting provider → Runs the authoritative name servers that store and answer your zone’s records (A, MX, TXT, etc.).
- Domain registrar / registry → Manages ownership of domain names within a top-level domain (
.com,.org, etc.) and publishes NS/DS records that delegate authority to your DNS host.
Some companies handle both functions (e.g., GoDaddy, Cloudflare), while others let you register in one place and host DNS somewhere else.
7.2 Common DNS Record Types
| Record Type | Purpose | Example |
|---|---|---|
| A | Maps domain → IPv4 address | example.com. IN A 192.0.2.1 |
| AAAA | Maps domain → IPv6 address | example.com. IN AAAA 2001:db8::1 |
| CNAME | Alias to another domain (not IP) | www.example.com. IN CNAME example.globalcdn.com. |
| ANAME / Alias | Provider-specific pseudo-record that behaves like a CNAME at the apex (e.g., Route 53 Alias, NS1 ANAME). | example.com. IN ALIAS edge.globalcdn.net |
| MX | Mail routing | example.com. IN MX 10 mail1.google.com. |
| TXT | Metadata (SPF, DKIM, domain verification) | example.com. IN TXT "v=spf1 include:_spf.google.com ~all" |
| NS | Authoritative name servers for a zone | example.com. IN NS ns1.dnsprovider.com. |
| SOA | Zone info (serial, refresh, retry) | example.com. IN SOA ns1 hostmaster 2025010101 3600 1800 1209600 86400 |
| PTR | Reverse DNS (IP → domain) | 1.2.0.192.in-addr.arpa. IN PTR example.com. |
| CAA | Restricts which Certificate Authorities can issue TLS certs | example.com. IN CAA 0 issue "letsencrypt.org" |
| SRV | Service-specific record (SIP, LDAP, Kerberos) | _sip._tcp.example.com. IN SRV 10 60 5060 sipserver.example.com. |
7.3 Apex (Naked) Domains
- The zone apex (e.g.,
example.com) represents the root of your domain. - DNS standards forbid placing a CNAME at the apex because it would conflict with other mandatory records (NS, SOA).
- Many providers offer ANAME/Alias features to simulate a CNAME at the apex by resolving the target to an A/AAAA record on the server side (e.g., Route 53 Alias, Cloudflare CNAME flattening).
- For subdomains like
www.example.com, you can safely use CNAME, ANAME/Alias, or A/AAAA records depending on the use case.
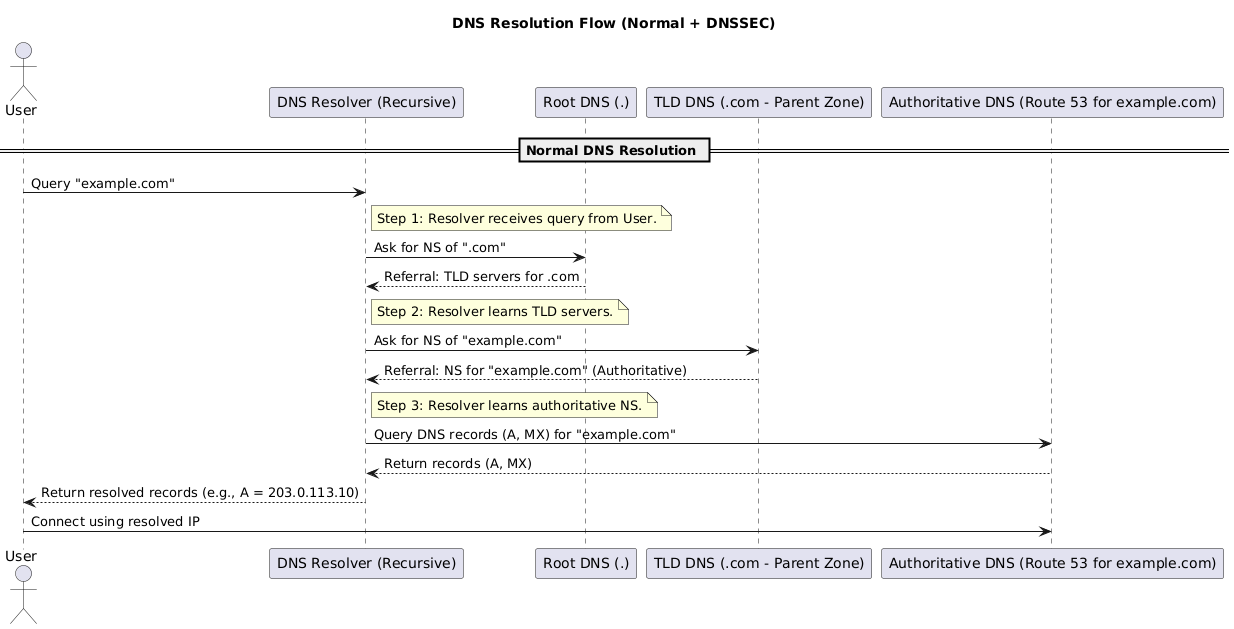
7.4 DNS Resolution Flow
- A user queries
example.comvia a recursive resolver (ISP, Google Public DNS, Cloudflare, etc.). - If the answer is uncached, the resolver asks the root servers which TLD (
.com) server is authoritative. - The resolver queries the TLD servers, which respond with the authoritative NS records for
example.com. - The resolver contacts the authoritative name servers for
example.com(your DNS host) and retrieves the requested record (A, MX, TXT, …). - The resolver caches the response based on its TTL and returns the answer to the user’s application, which then reaches out to the resolved endpoint.
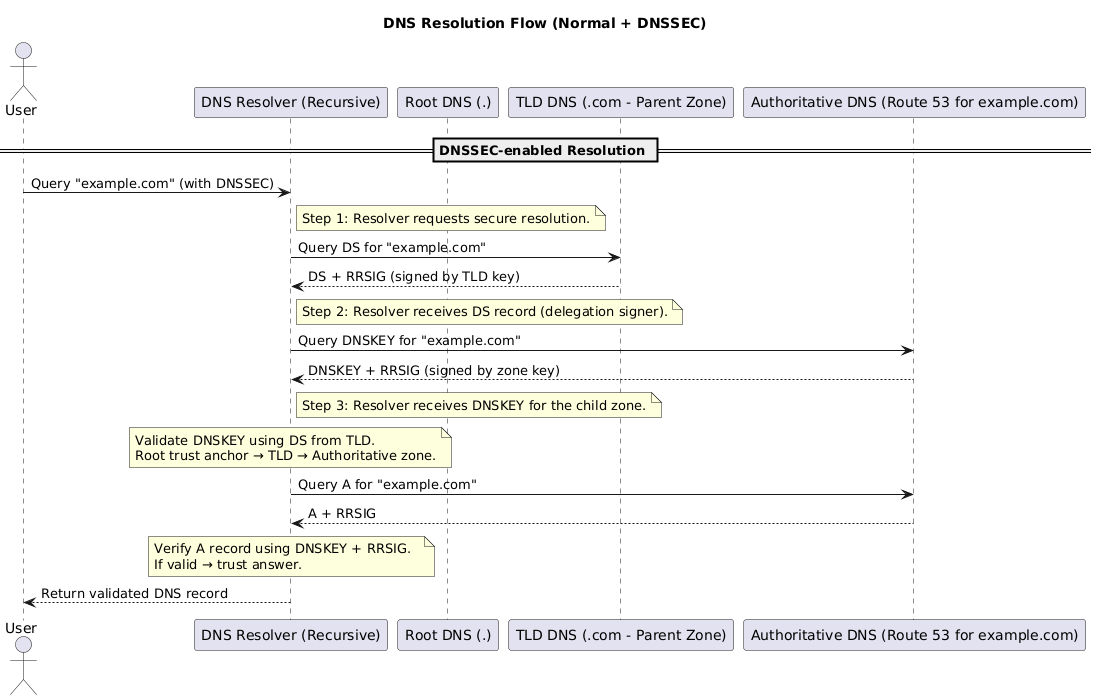
7.5 DNSSEC Overview
DNSSEC (Domain Name System Security Extensions) protects against forged DNS data by cryptographically signing DNS responses. It ensures authenticity and integrity, but it does not encrypt traffic.
Without DNSSEC, attackers can poison resolver caches or spoof responses. With DNSSEC, resolvers reject tampered data because signatures fail validation.
7.5.1 Key Concepts
- Digital Signatures: Authoritative servers sign each RRset with a private key; resolvers validate using the corresponding public key.
- DNSSEC Records:
- DNSKEY → Publishes the public keys for the zone.
- DS (Delegation Signer) → Parent zone pointer to the child zone’s key, extending the trust chain.
- RRSIG → Signature attached to each signed record set.
- Chain of Trust: Root (trust anchor) → TLD → Authoritative zone. Every delegation must be signed to keep the chain intact.
7.5.2 Roles and Responsibilities
- Root & TLD Operators: Maintain signed parent zones and publish DS records for child delegations.
- Zone Owners / DNS Hosts: Generate keys, sign zones, and supply DS records to the registrar.
- Recursive Resolvers: Validate signatures and refuse bogus data. Many public resolvers already validate DNSSEC by default.
- End Users: No action required; they benefit from resolvers rejecting tampered responses.
7.5.3 Validation Flow
- Resolver requests the DS record for
example.comfrom the TLD; verifies the response using the TLD’s signature. - Resolver requests the DNSKEY record set from
example.com’s authoritative servers and verifies it against the DS digest. - Resolver fetches the desired record (e.g.,
A example.com) along with its RRSIG. - Using the validated DNSKEY, the resolver checks the RRSIG. If it validates, the answer is accepted and cached; otherwise the response is discarded as suspicious.
7.6 Route 53 Hosted Zone Resolution Flow
- You create a Hosted Zone in Route 53 for your domain (
example.com). - Route 53 assigns 4 authoritative name servers (NS records) for the domain.
- You add DNS records (A, CNAME, MX, TXT, etc.) inside the hosted zone.
- When a client queries
example.com, the DNS resolver follows the chain:- Root → TLD → Route 53 authoritative NS (Amazon-managed).
- Route 53 authoritative servers return the DNS record (e.g., A record with an IP).
- Resolver caches and returns result to user → user connects to the target resource.
8. VPN
Note VPN builds on top of IPSec, for details on how IPSec works, see 3.4 Layer 3 & 5–6 - IPsec
8.1 Site-to-Site VPN
- Purpose:
- Site-to-Site VPN = Network ↔ Network
- Connects an entire on-premises network (via a CGW) to an AWS VPC network (via a VGW or TGW).
- Used for hybrid cloud connectivity, extending datacenter or branch office networks into AWS.
- Example: Your office LAN can securely reach EC2 instances inside VPCs.
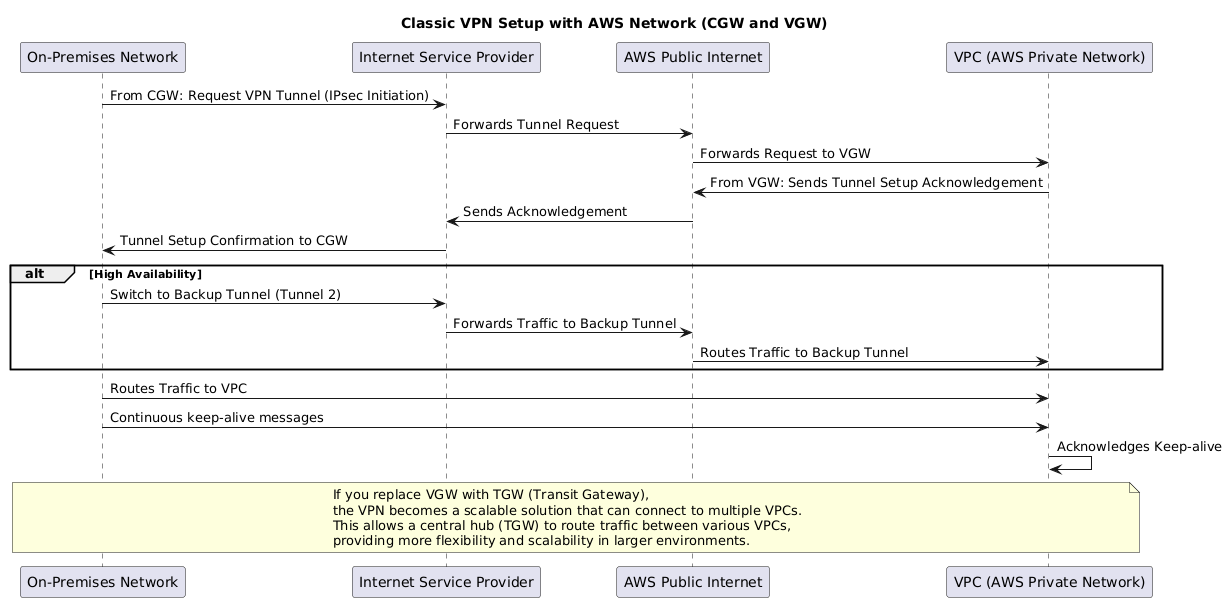
8.1.1 Connectivity Types
Keep in mind, VPN connections traverse the public Internet before reaching AWS’s network. Because of this, the routing path and how routes are exchanged are critical.
- Static VPN
- Route: Static routes in route tables (manual setup).
- Pros: Simple setup.
- Cons: No load balancing or failover.
- Dynamic VPN
- Route: Uses BGP for automatic route exchange.
- Pros: High availability, automatic failover, and load balancing.
- Cons: More complex setup.